I’m going to answer the question you asked, then the question you might mean. The MAC address is the physical “serial number” of the network card in your device. It’s supposed to be unique worldwide. It’s only used by machines on your local netwo. IP Source Address Spoofing. IP source address spoofing is the process of intentionally configuring an IP address to impersonate another host or device on the network. This type of action is typically performed by a malicious actor attempting to circumvent access control restrictions that it.
- Mac Address Spoofing Tool
- Mac Address Spoofing Software
- Mac Address Spoofing Blocking Software Free
- Ip Address Spoofing Software
- Mac Address Spoofing Blocking Software Download
- Stop Mac Address Spoofing
MAC address short form of Media Access Control Address, is a address that uniquely identifies you computer. For every network card on your computer there is a MAC address, which comes built-in. This applies to all types of network cards be it Ethernet or WiFi. Whether you are using a wired connection or wireless one, you do need to transfer data from your computer to some other computer. But how does the other computer find your computer? That is where addresses come in. These addresses are actually hard-coded into the network card. These are given to a network adapter in the manufacturing stage itself. And since these addresses are permanent, they are generally used to prevent devices from accessing a particular network. Does this mean they can never be changed? Well, yes. Then what is this article about? One simple word, MAGIC ! The hard-coded MAC address can never be changed but you can spoof the MAC address in your operating system. But before moving on with our spoofing mac address OS X trick, let’s see what does a MAC address look like.
Hi, I'm using a HP Procurve 2626, Is there a way to detect/block a PC with a spoofed MAC address? We already configured port security on the switch (allowed only 1 mac address on 1 port) but the users only used another PC(Laptop) and used an application to spoof the mac address of the allowed PC's mac address using the same network cable or Switch port. I bet by now you should know the power of spoofing your MAC Address. MAC address can actually be changed directly from Windows but the easiest way is to just a free program called Technitium MAC Address Changer. To change your MAC address, run the program, click the Random MAC Address button followed by the Change Now! Like Ethernet, 802.11 makes use of a device's MAC address to uniquely identify it on the network. However, it's trivial to change the MAC address of a wireless interface under most operating systems.
MAC address is the lower sub-layer of the data link layer in the Open System Interconnection (OSI) model. It is a six-byte number. MAC address is also often referred as the Physical Address. A possible MAC address can be 2F-4D-5B-6E-2A-9C. As you can clearly see it is a 12-digit hexadecimal or 48 bits number. The first 6 digits helps to find the manufacturer, while the last six digits find your device. The manufacturers have already got this special number sequence to find themselves as manufactures. Dell has 00-14-22 at the beginning, Cisco has 00-40-96 and so on. These are often referred as OUI or Organizationally Unique Identifier. The last 6 digits or three bytes is the NIC (Network Interface Controller) specifier. A possible question now arises that why would someone like to change their MAC address? It is for so many reasons. If your network limits access to some MAC addresses, then you can change it and have the network access. If a network filters out access based on MAC address, then you can sniff out a legitimate MAC address, change your MAC address and connect. If you want privacy over surfing or any network activity, you could change your MAC address and be untraceable. You can also bypass certain network restriction by spoofing an authorized MAC address. There are many more reasons one might want to change his/her computers MAC address. Let’s not go to too much detail and begin.
Before changing the MAC address on Mac Computer let’s see how can you look up your MAC address. There are generally three ways to go about it.
Read Also:
1. Easy
Press and hold the option key, now click on the WiFi icon from the menu bar. You will see couple of things here, look out for “Address:”. The next 12 hexadecimal digits following it is your MAC address. And it tells you the connection name also. Wasn’t it easy?
2. Medium
Mac Address Spoofing Tool
WiFi Spoof MAC
Open up System Preference and now move on to Network section. Select the network via which you are connected and then click on the Advanced button. Now, select the Hardware tab, the first thing you will see is MAC address.
3. Advanced
This is the toughest one of the all. Open up the terminal and type the command:
ifconfig en0 grep ether
Mac Address Spoofing Software
This actually shows the MAC address for en0 interface. Just change the name of the interface and look for yourself. Was it that difficult?
Now, that we know our MAC address, let us generate some random MAC addresses, in the terminal just type:
openssl rand -hex 6 sed ‘s/(.)/1:/g; s/.$//’
This will generate a random MAC address. The format of MAC address as earlier mentioned in this article is in the form xx:xx:xx:xx:xx:xx, if you already have one in mind you don’t need to generate one. But keep in mind it should be 12 digits hexadecimal.
changing mac address on macOS sierra or OS X Yosemite or OS X El Capitan or any Mac OS X is just one command, open up the terminal and type in:
sudo ifconfig en0 ether xx:xx:xx:xx:xx:xx
You need to have administrative privileges to change the MAC address, hence it will ask for the password. It is best recommended that you disconnect from the network while changing your MAC address and then again reconnect after successfully changing it. Also, make a note of your default hardware MAC address. Some the MAC use Wi-Fi instead of ether in the above command. if you meet any problem try to use Wi-Fi. Remove the xx:xx:xx:xx:xx:xx with your MAC address generated or you have in mind. And also replace en0 with any other interface name that you are using. If you don’t know the interface name, you should check it from the above mentioned steps. To confirm that it has been changed you could use any of the above mentioned way. If you are changing your MAC address to get privacy you better generate random MAC address.
After changing the MAC address on your OS X or sierra or yosemite or el capitan it might be possible that you meet network issues, in that case make sure you turn off and then turn on your network device. You can use the method and get around with any blocking. It sounded a very difficult task at the beginning, but even you can see how easy it was. Let me know, how did it go for you?
Mac Address Spoofing Blocking Software Free

MAC spoofing is a technique for changing a factory-assigned Media Access Control (MAC) address of a network interface on a networked device. The MAC address that is hard-coded on a network interface controller (NIC) cannot be changed. However, many drivers allow the MAC address to be changed. Additionally, there are tools which can make an operating system believe that the NIC has the MAC address of a user's choosing. The process of masking a MAC address is known as MAC spoofing. Essentially, MAC spoofing entails changing a computer's identity, for any reason, and it is relatively easy.[1]
Motivation[edit]
The changing of the assigned MAC address may allow the bypassing of access control lists on servers or routers, either hiding a computer on a network or allowing it to impersonate another network device. MAC spoofing is done for legitimate and illicit purposes alike.
New hardware for existing Internet Service Providers (ISP)[edit]
Many ISPs register the client's MAC address for service and billing services.[2] Since MAC addresses are unique and hard-coded on network interface controller (NIC) cards,[1] when the client wants to connect a new gadget or change their existing gadget, the ISP will detect different MAC addresses and the ISP might not grant Internet access to those new devices. This can be circumvented easily by MAC spoofing. The client only needs to spoof the new device's MAC address to the MAC address that was registered by the ISP.[2] In this case, the client spoofs their MAC address to gain Internet access from multiple devices. While this seems like a legitimate case, MAC spoofing new gadgets can be considered illegal if the ISP's user-agreement prevents the user from connecting more than one device to their service. Moreover, the client is not the only person who can spoof their MAC address to gain access to the ISP. Hackers can gain unauthorized access to the ISP via the same technique. This allows hackers to gain access to unauthorized services, and the hacker will be hard to identify because the hacker uses the client's identity. This action is considered an illegitimate use of MAC spoofing and illegal as well. However, it is very hard to track hackers that are utilizing MAC spoofing.[3]
This also applies to customer-premises equipment, such as cable and DSL modems. In cases where the provider leases the equipment to the customer on a monthly basis, the CPE has a hard-coded MAC address which is on a list known to the provider's distribution networks, allowing service to be established as long as the customer is not in billing arrears. In cases where the provider allows customers to provide their own equipment (and thus avoid the monthly leasing fee on their bill,) the provider requires that the customer give them the MAC address of their equipment before service will be established.
Epson Connect consists of Epson Email Print, Remote Print and Scan To Cloud. Description:This file contains the EpsonNet Config Utility v4.9.5.EpsonNet Config is a configuration utility for administrators to configure the network interface. For setup instructions, please see our page.Compatible systems:Windows 10 32-bit, Windows 10 64-bit, Windows 8.1 32-bit, Windows 8.1 64-bit, Windows 8 32-bit, Windows 8 64-bit, Windows 7 32-bit, Windows 7 64-bit, Windows XP 32-bit, Windows XP 64-bit, Windows Vista 32-bit, Windows Vista 64-bitNote:This file applies to numerous Epson products and may be compatible with operating systems that your model is not. Where i download software in mac.
Fulfilling software requirements[edit]
Some software can only be installed and run on systems with pre-defined MAC addresses as stated in the software end-user license agreement, and users have to comply with this requirement in order to gain access to the software. If the user has to install different hardware due to malfunction of the original device or if there is a problem with the user's NIC card, then the software will not recognize the new hardware. However, this problem can be solved using MAC spoofing. The user just has to spoof the new MAC address as to mimic the MAC address that was registered by the software.[citation needed] This activity is very hard to define as either legitimate or illegitimate reason for MAC spoofing. Legal issues might arise if the user grants access to the software on multiple devices simultaneously. At the same time, the user can obtain access to software for which he or she has not secured a license. Contacting the software vendor might be the safest route to take if there is a hardware problem preventing access to the software. Software may also perform MAC filtering because the software does not want unauthorized users to gain access to certain networks to which the software grants access. In such cases MAC spoofing can be considered a serious illegal activity and can be legally punished.[4]
Identity masking[edit]
If a user chooses to spoof their MAC address in order to protect the user's privacy,[citation needed] this is called identity masking. One might wish to do this because, as an example, on a Wi-Fi network connection a MAC address is not encrypted. Even the secure IEEE 802.11i-2004 (WPA) encryption method does not prevent Wi-Fi networks from sending out MAC addresses.[citation needed] Hence, in order to avoid being tracked, the user might choose to spoof the device's MAC address. However, hackers use the same technique to maneuver around network permissions without revealing their identity. Some networks use MAC filtering in order to prevent unwanted access. Hackers can use MAC spoofing to get access to a particular network and do some damage. Hackers' MAC spoofing pushes the responsibility for any illegal activity onto authentic users. As a result, the real offender may go undetected by law enforcement.[citation needed]
MAC Address Randomization in WiFi[edit]
To prevent third parties from using the MAC address to track devices, Android, Linux, iOS, and Windows[5] have implemented MAC addressrandomization. In June 2014, Apple announced that future versions of their iOS platform would randomize MAC addresses for all WiFi connections. The Linux kernel has supported MAC address randomization during network scans since March 2015,[6] but drivers need to be updated to use this feature.[7] Windows has supported it since the release of Windows 10[5] in July 2015.
Controversy[edit]
Although MAC address spoofing is not illegal, its practice has caused controversy in some cases. In the 2012 indictment against Aaron Swartz Internet hacktivist, who was accused of illegally accessing files from JSTOR digital library, prosecutors claimed that because he had spoofed his MAC address it showed purposeful intent to commit criminal acts.[4] In June 2014, Apple announced that future versions of their iOS platform would randomize MAC addresses for all WiFi connections, making it more difficult for internet service providers to track user activities and identities, which resurrected moral and legal arguments surrounding the practice of MAC spoofing among several blogs and newspapers.[8]
Limitations[edit]
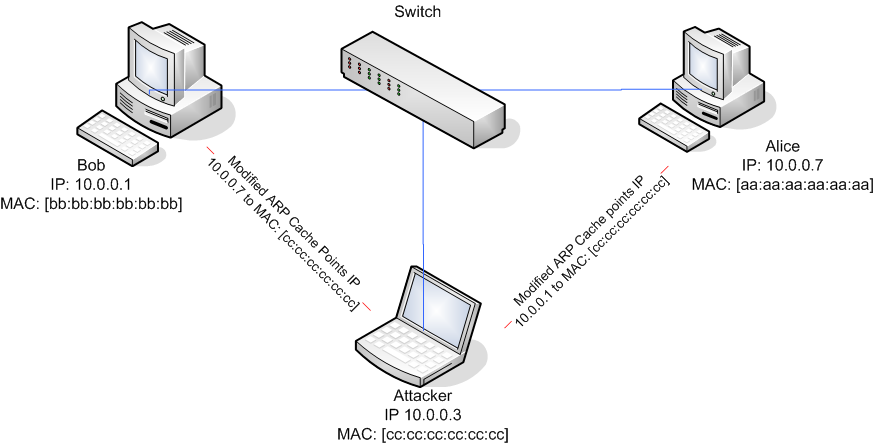
MAC address spoofing is limited to the local broadcast domain. Unlike IP address spoofing, where senders spoof their IP address in order to cause the receiver to send the response elsewhere, in MAC address spoofing the response is usually received by the spoofing party if switch is not configured to prevent MAC spoofing.
See also[edit]
Ip Address Spoofing Software
- ifconfig, linux utility capable of changing MAC address
References[edit]
Mac Address Spoofing Blocking Software Download
- ^ abCardenas, Edgar D. 'MAC Spoofing--An Introduction'. GIAC Security Essentials Certification. SANS Institute. Retrieved 8 February 2013.
- ^ ab'MAC Spoofing'. Royal Canadian Mounted Police. Research and Development Section in Collaboration with the NCECC’s Technology Unit. Archived from the original on 23 June 2012. Retrieved 8 February 2013.
- ^Gupta, Deepak; Gaurav Tiwari (4 November 2009). 'MAC SPOOFING AND ITS COUNTERMEASURES'(PDF). International Journal of Recent Trends in Engineering. 2 (4): 21. Retrieved 8 February 2013.
- ^ abIndictment against Aaron Swartz
- ^ abhttp://papers.mathyvanhoef.com/asiaccs2016.pdf
- ^https://w1.fi/cgit/hostap/plain/wpa_supplicant/ChangeLog
- ^https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=ad2b26abc157460ca6fac1a53a2bfeade283adfa
- ^Change MAC Address: Use Public WiFi Signals Without Any Limits, Not To Mention Serious Privacy Benefits
